Secrets Management Implementation with CyberArk

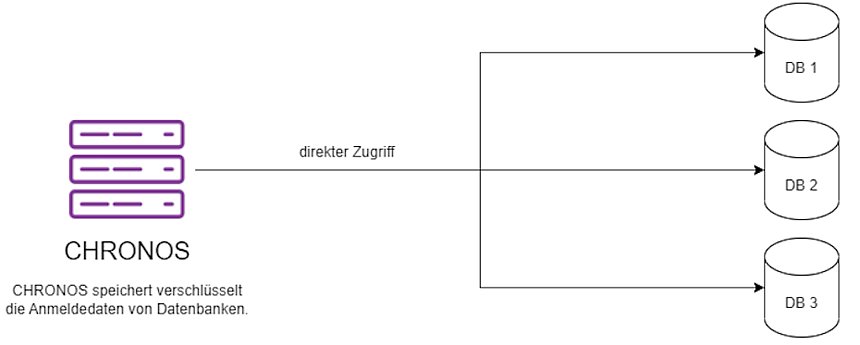
With the CHRONOS CyberArk module, all database connection data to stored databases can be read from CyberArk, centrally secured.
Secrets management is a best practice in the cyber security industry to enforce security policies for non-human identities. Organizations gain assurance that only authenticated and authorized users can access resources. In CHRONOS, a web service interface to the Secrets query of the CyberArk Identity Security Platform has been integrated to implement this security strategy. This eliminates the need to store sensitive database credentials in CHRONOS and eliminates the need to change passwords.
Secrets Management Advantages:
- Centralization: Secrets management is automated and centralized.
- Restriction of access: Access to secrets is restricted to applications/tools/processes.
- Encryption: All secrets are stored in encrypted form.
- Validity period: Secrets can be limited in time.
- Monitoring: all interactions are recorded.
-
-
-
Example:
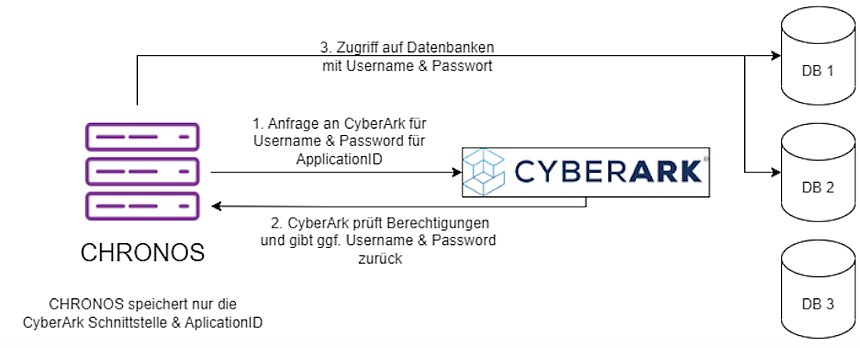
CHRONOS configures a database connection with password stored in encrypted form. With the CyberArk interface, passwords and usernames are no longer stored. Only the interface and ApplicationID are required. CHRONOS starts a request for a specific ApplicationID through CyberArk and wants to know the current username and password. CyberArk itself verifies that CHRONOS is authorized to obtain this information for the ApplicationID.
After verification CHRONOS gets access to the database.


![[Translate to en:] [Translate to en:]](https://www.csp-sw.com/fileadmin/_processed_/4/0/csm_Blogbeirag_Eduard_im_Beirat_80166e698c.jpg)